BPM that brings structure, speed and control to your operations
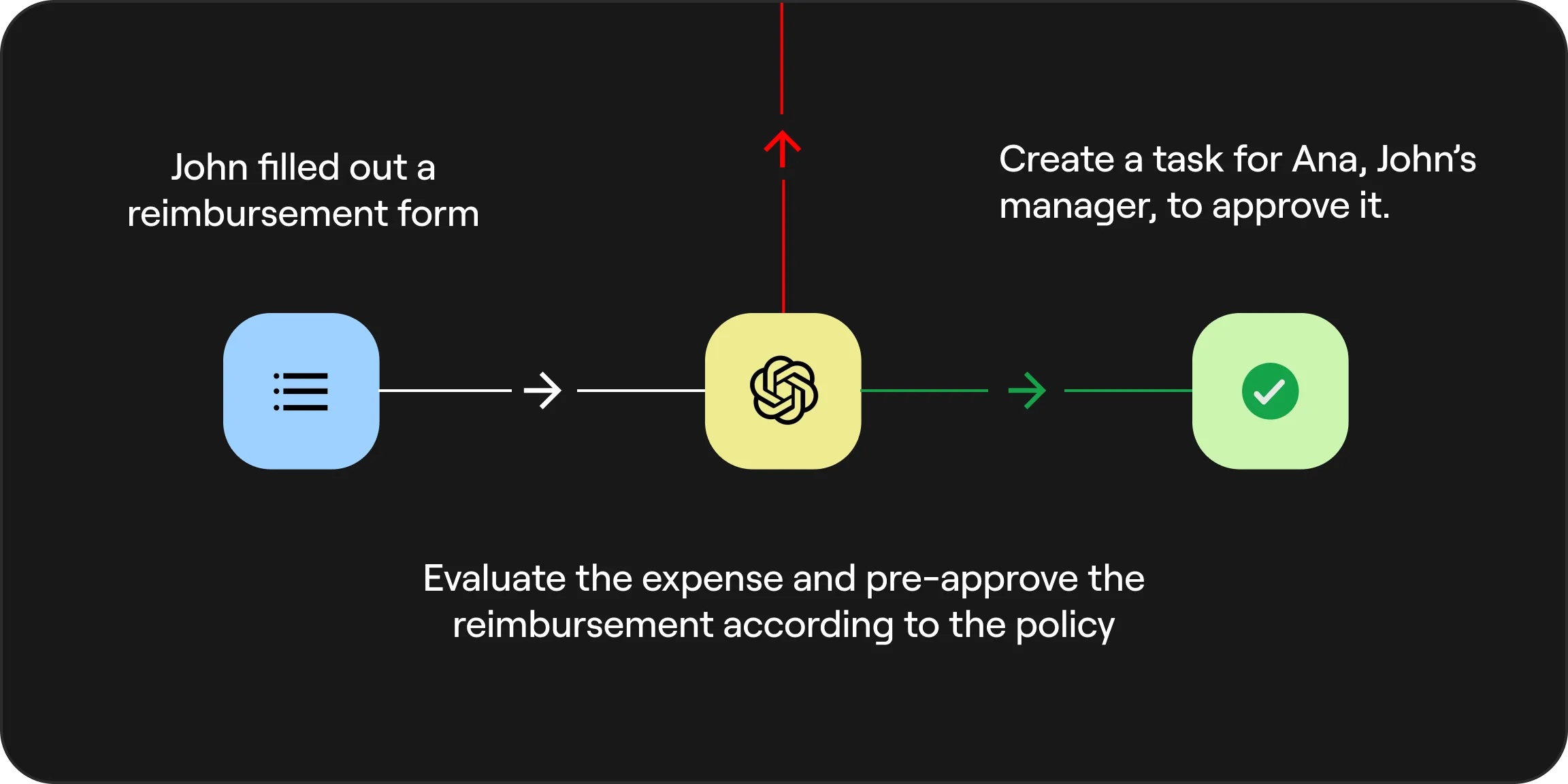
Replace scattered tasks and manual steps with standardized, automated workflows. Gain full visibility, reduce errors, and ensure your processes actually get followed.
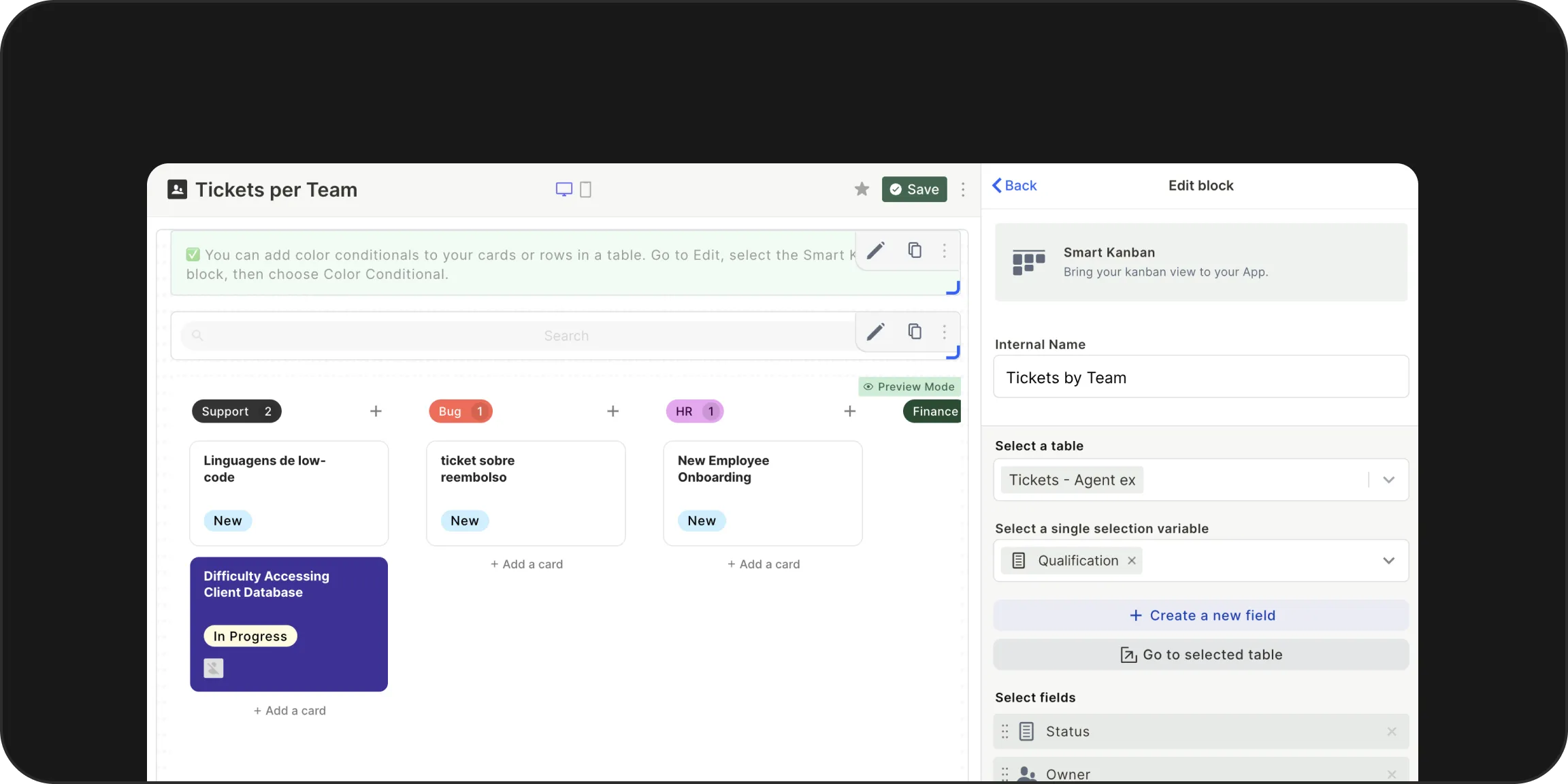
Process Management (BPM): Powerful process modeling
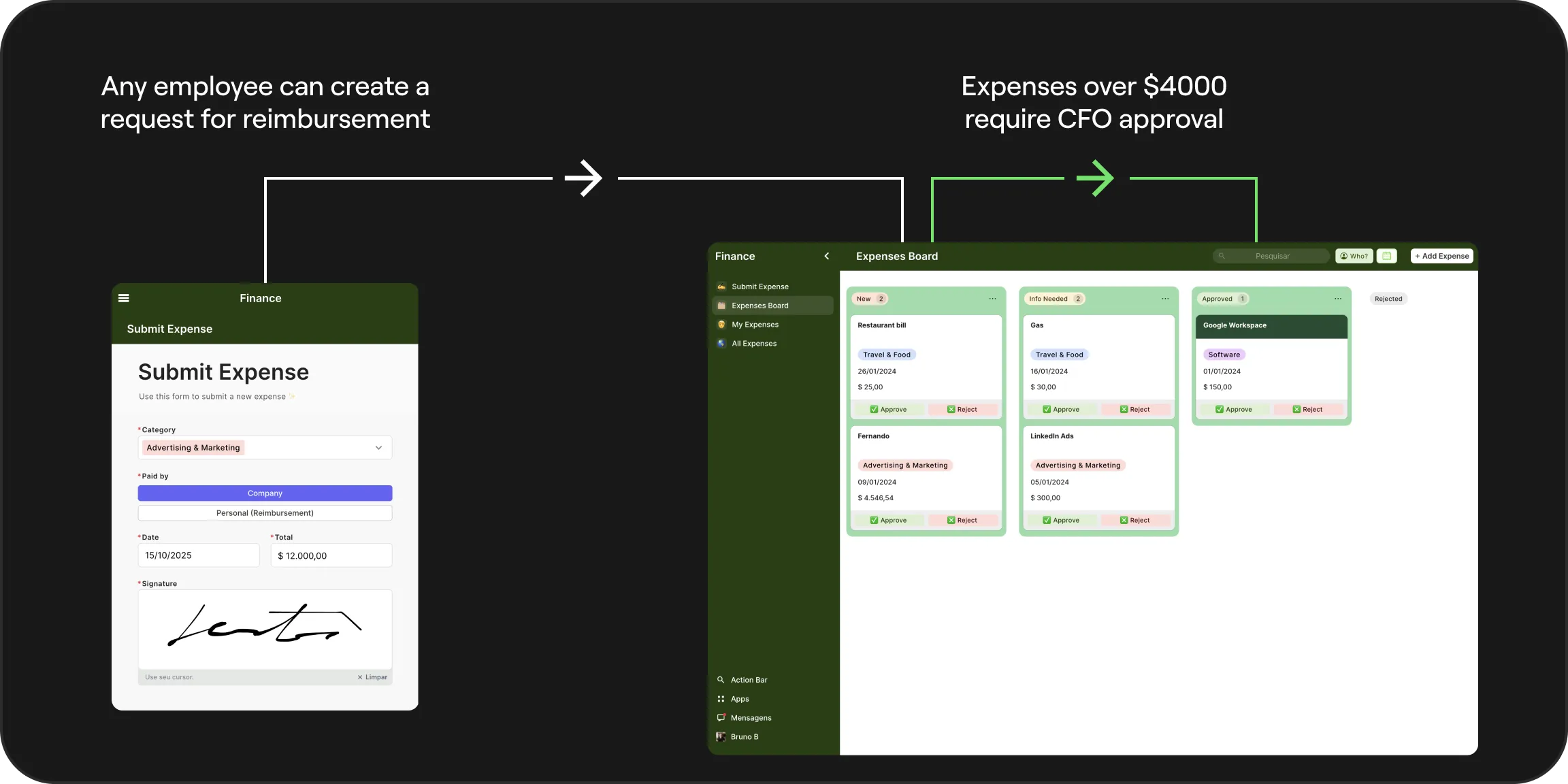
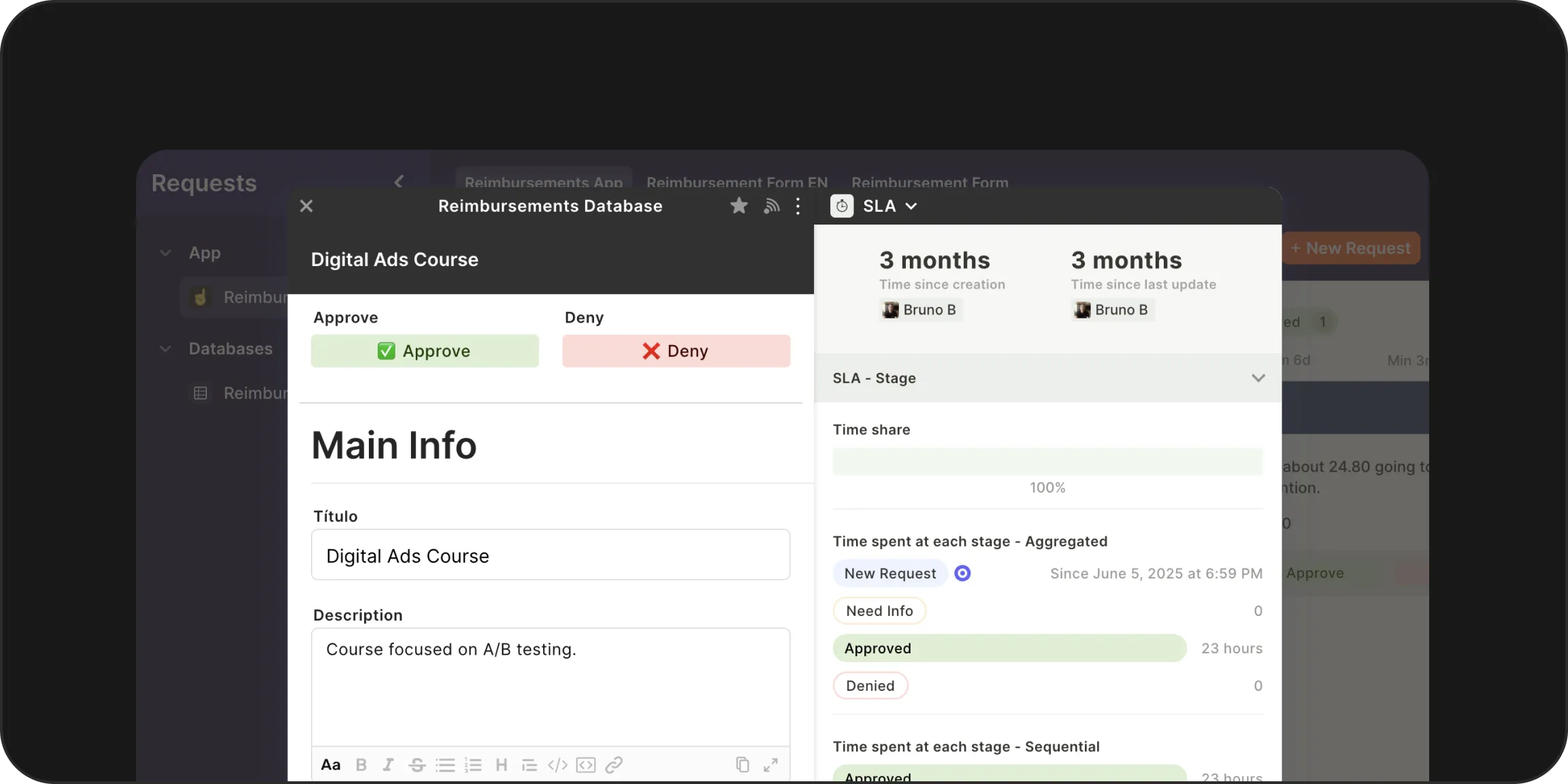
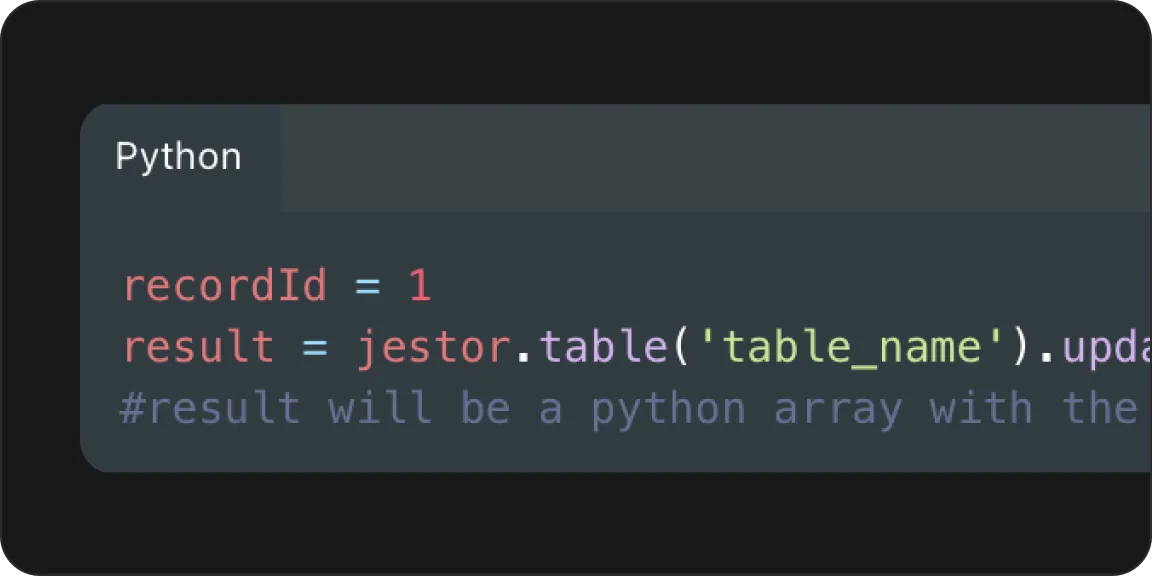
Process Automation (BPA): Replace manual work
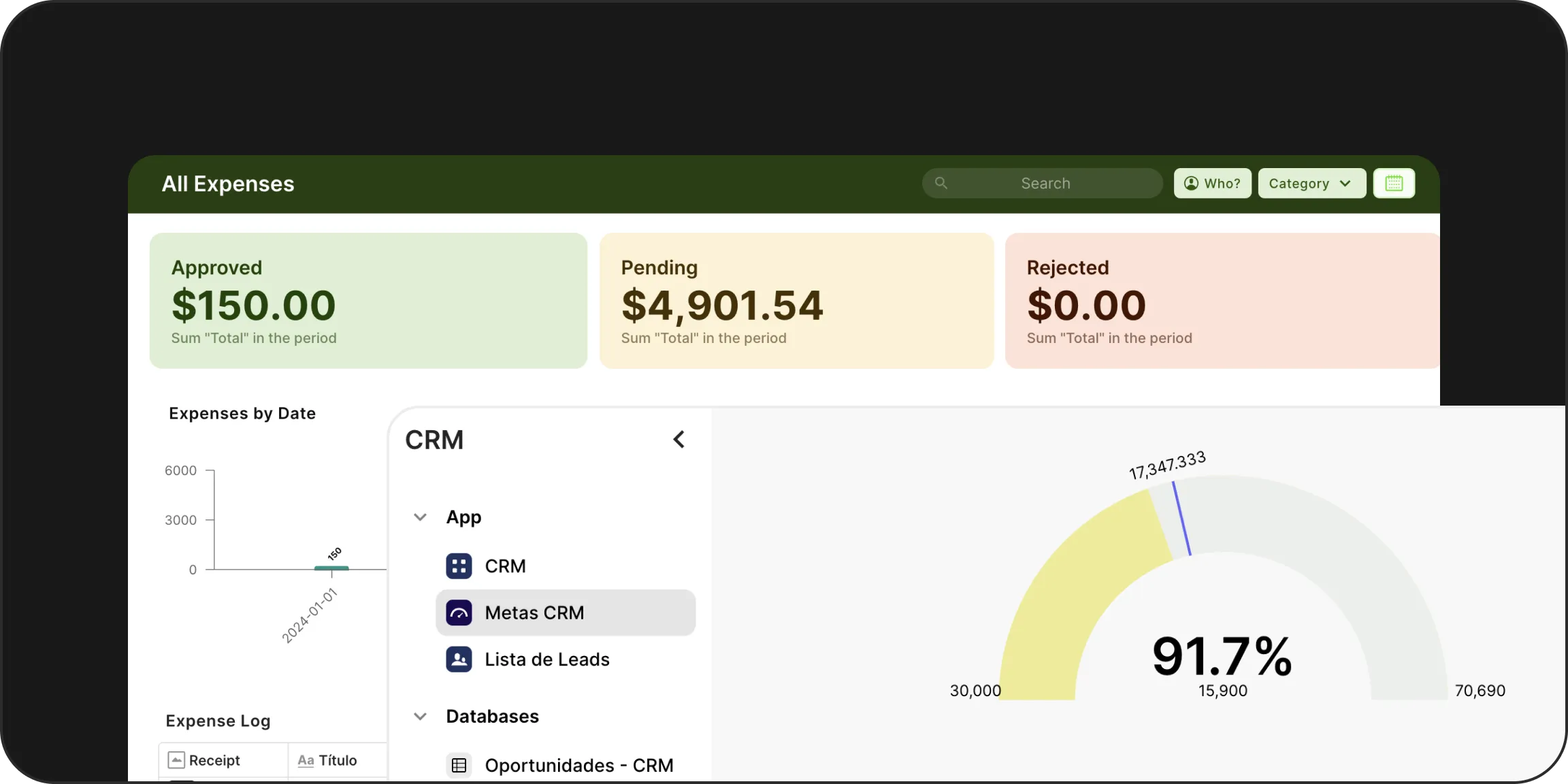
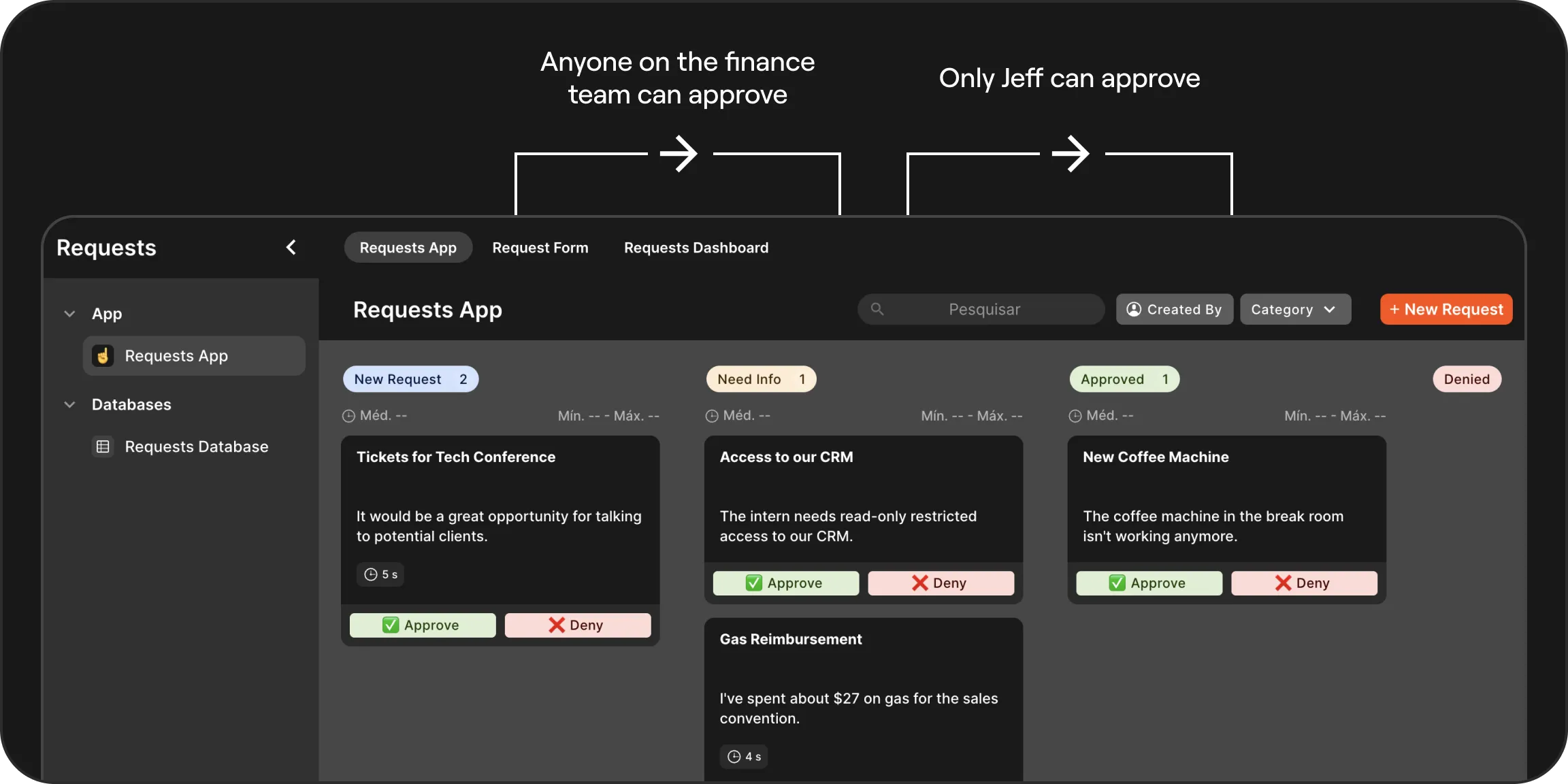
Powerful Security and Flexible Permission Settings
What do the customers say?
"19 spreadsheets replaced — now turned into standardized workflows with all the control and security that Jestor offers."
"Jestor helped us replace manual work that was previously done using spreadsheets, Google Docs, WhatsApp, and Pipefy."